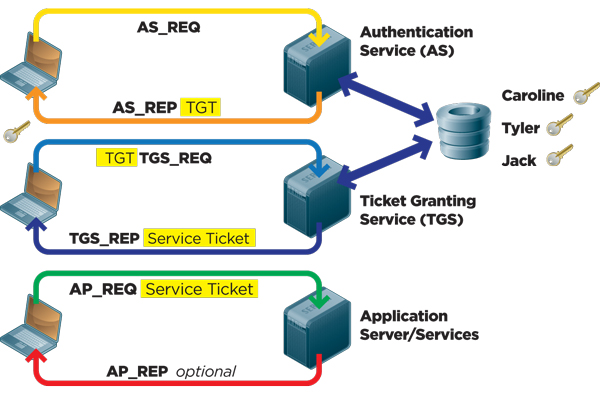
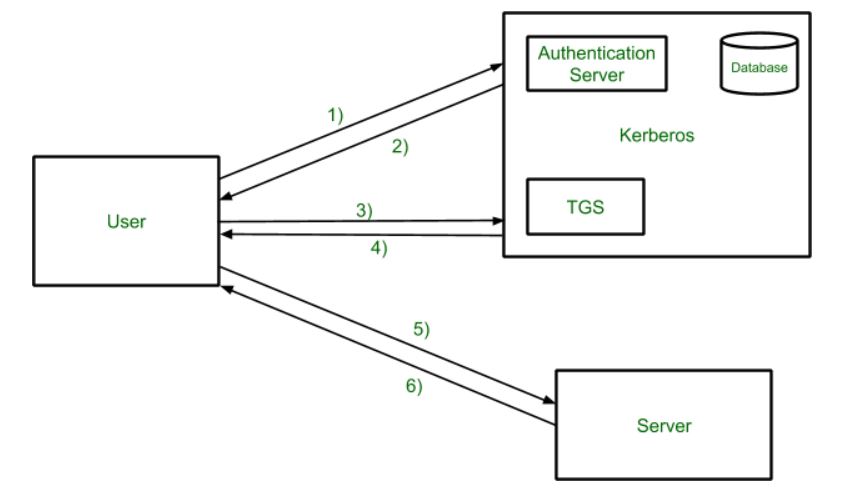
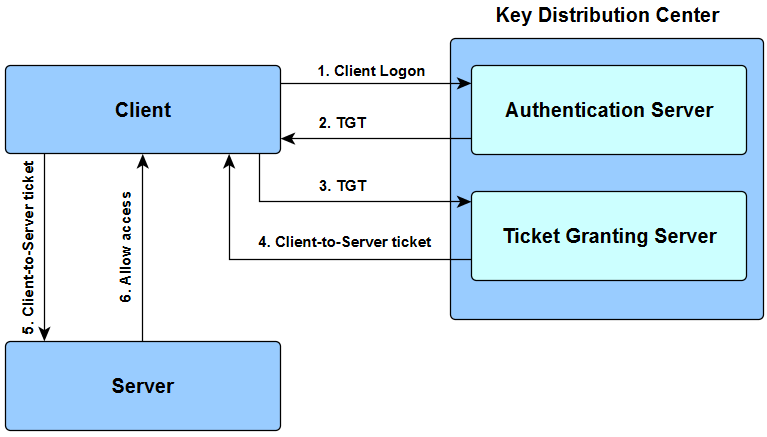
Most of the systems implement this capability. Client uses TGT to request access.

The Kerberos Ticket Instant Refresh And Security Legacy Protocols Seven It Blog
Password configured to the ADMIN user.
Kerberos authentication process step by step. Go to IIS manager Sites Tab Select the web application and in the middle pane double click on Authentication under IIS section. The steps followed from Step 9 shows you the configuration when you want to configure double hop ie delegate the logged in account to a backend server for eg a sql. In the absence of an authentication a process or a user can pose itself to be a trusted identity and gain access to the data.
Then create a user in Active Directory server for authentication. Kinit and proceed with spark-submit kinit -kt KERBEROS_KEYTAB_PATH KERBEROS_PRINCIPAL step 2. Create a directory named TEST and give the user named www-data permission over this directory.
This article will help the SharePoint administrators who want to configure the Kerberos Authentication in their SharePoint web applications. You might be interested in a step by step demo for setting up a Kerberised cluster. Configure the Nginx server to request the PAM authentication to users trying to access this directory.
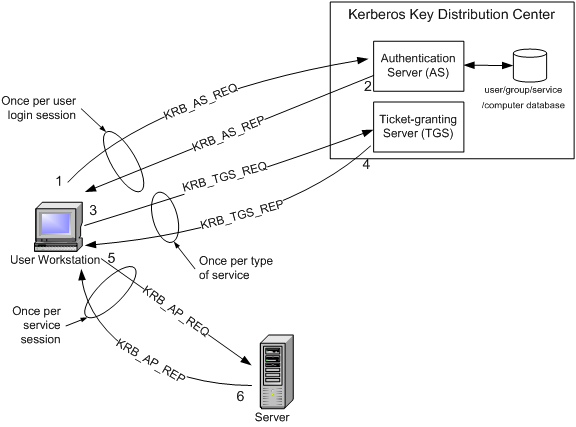
The user logs on to the workstation and requests service on the host. Steps 1-8 should be sufficient when you want Kerberos for the site to be configured only for single HOP. Using Kerberos authentication within a domain or in a forest allows the user or service access to resources permitted by administrators without multiple requests for credentials.
Create a new account inside the Users container. To understand the conceptual framework see Kerberos authentication. In authentication check the Kerberos checkbox and in external ID fill the value FQDN 10-Create connection in HANA Studio with SSO Create system in HANA Studio.
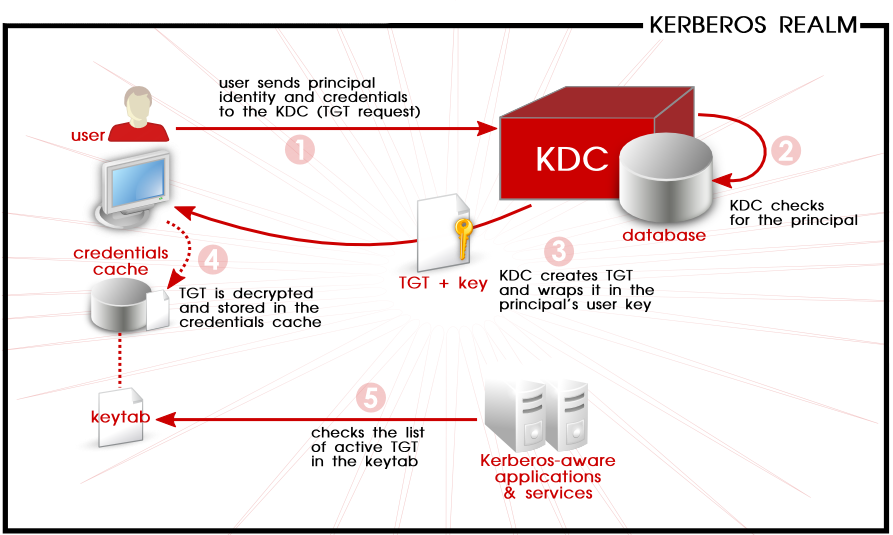
The KDC creates a ticket. The Authorization Sever encrypts the results using a key derived from the users password and sends a. Mkdir varwwwhtmltest chown www-datawww-data varwwwhtmltest -R.
After initial domain sign on through Winlogon Kerberos manages the credentials throughout the forest whenever access to resources is attempted. Configure Kerberos in IIS. This request consists of the PC Client TGT and an authenticator.
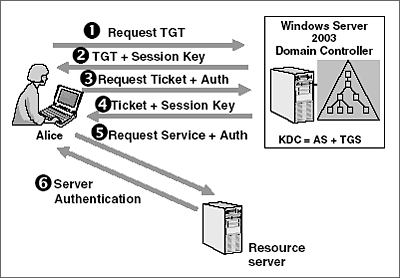
When the client logs into the domain a Ticket-Granting Ticket TGT request is sent across to Key Distribution Center KDC 2. Create a new account named. You must log on to the domain controller computer as a user with administrator permissions.
The below steps will take you through the setup of Kerberos for a site. Run klist and verify Kerberization is correctly working for. Active Directory Users and Computers.
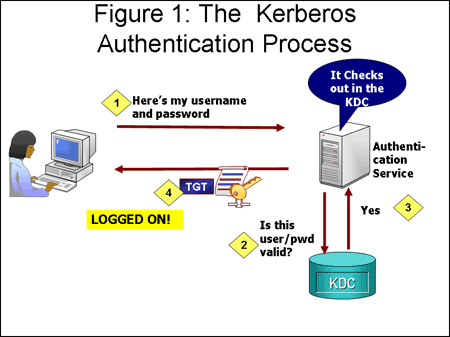
The Kerberos Authentication Service authenticates the user and issues a TGT ticket. Open your Central Administrator site. In the phase of the user and password choose Authenticated by current OS user.
A Ticket-Granting Ticket TGT request is sent to a Kerberos KDC. Creating user identity which will be used for active directory authentication. Here are the most basic steps taken to authenticate in a Kerberized environment.
In the Authentication dialog select Windows Authentication. The workstation sends a message to the Authorization Server requesting a ticket granting ticket TGT. Kerberos Authentication Steps.
Likewise where is Kerberos authentication used. Client requests an authentication ticket TGT from the Key Distribution Center KDC The KDC verifies the credentials and sends back an encrypted TGT and session key The TGT is encrypted using the Ticket Granting Service TGS secret key. In the extract below you will see all the steps involved in Kerberos Authentication.
PC Client logs on the domain. The Kerberos KDC responds by returning a TGT and a session key to client. The KDC creates a ticket for the file server.
Creating new web application with Kerberos Authentication. We have captured step by step process of how to configure Kerberos Authentication in SharePoint 2013. Set Kerberos as Top Authentication provider over NTLM and uncheck Enable Kernel-mode authentication.
On the domain controller open the application named. The client uses the file ticket to authenticate. KDC checks the clients credentials.
These are the steps in Kerberos Authentication. The Authorization Server verifies the users access rights in the user database and creates a TGT and session key. The Kerberos KDC returns a TGT and a session key to the PC Client.
A ticket request for the application server is sent to the Kerberos KDC. This account will be used to authenticate.
Kerberos Authentication 101 Understanding The Essentials Of The Kerberos Security Protocol Redmondmag Com

Kerberos Authentication Flow For Browser Based Applications Provided By The As Abap Sap Blogs
Configuring Kerberos Authentication Protocol Datasunrise Data Db Security
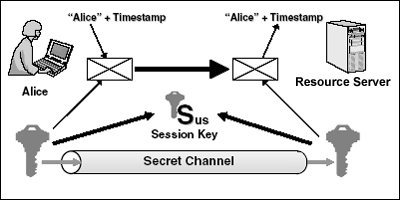
Five Steps To Using The Kerberos Protocol
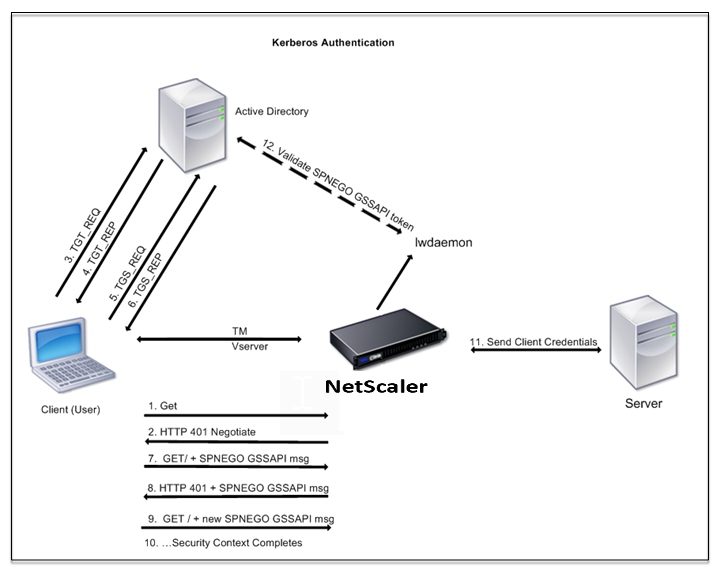
How Citrix Adc Implements Kerberos For Client Authentication
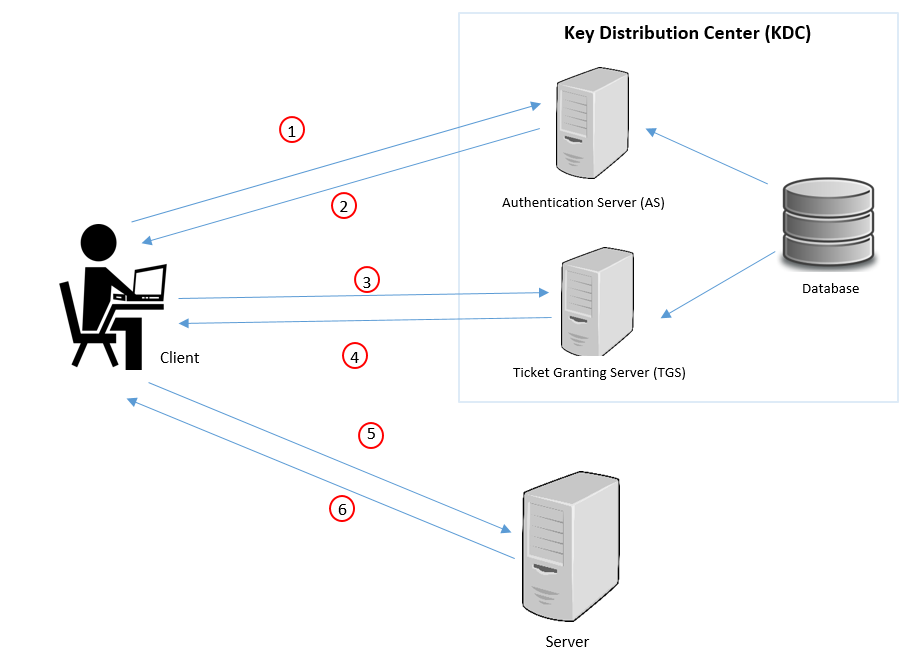
Kerberos The Computer Network Authentication Protocol By Dewni Weeraman Medium

Kerberos Authentication Protocol Download Scientific Diagram
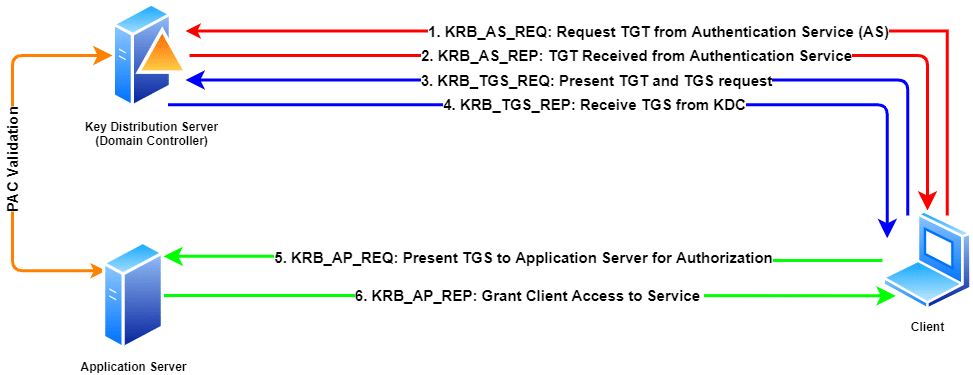
What Is Kerberos Understanding Kerberos What Is It How Does It Work
Five Steps To Using The Kerberos Protocol
Chapter 3 Using Kerberos Red Hat Enterprise Linux 6 Red Hat Customer Portal
Intel Amt Sdk Implementation And Reference Guide

1 A Simplified Version Of The Kerberos Authentication System Both The Download Scientific Diagram
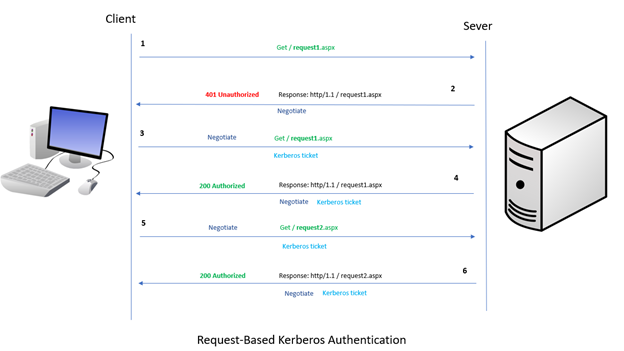
Request Based Versus Session Based Kerberos Authentication Or The Authpersistnonntlm Parameter Microsoft Tech Community
Kerberos Authentication Protocol Blog On Information Security And Other Technical Topics